Ldap Authentication for Bare Metal
Set up Configurations in openmetadata.yaml
Authentication Configuration
The following configuration controls the auth mechanism for OpenMetadata. Update the mentioned fields as required.
For the LDAP auth we need to set:
OpenMetadata Specific Configuration :
provider: ldappublicKeyUrls: {http|https}://{your_domain}:{port}}/api/v1/system/config/jwksauthority: {your_domain}enableSelfSignup: This has to be false for Ldap.
Mandatory LDAP Specific Configuration:
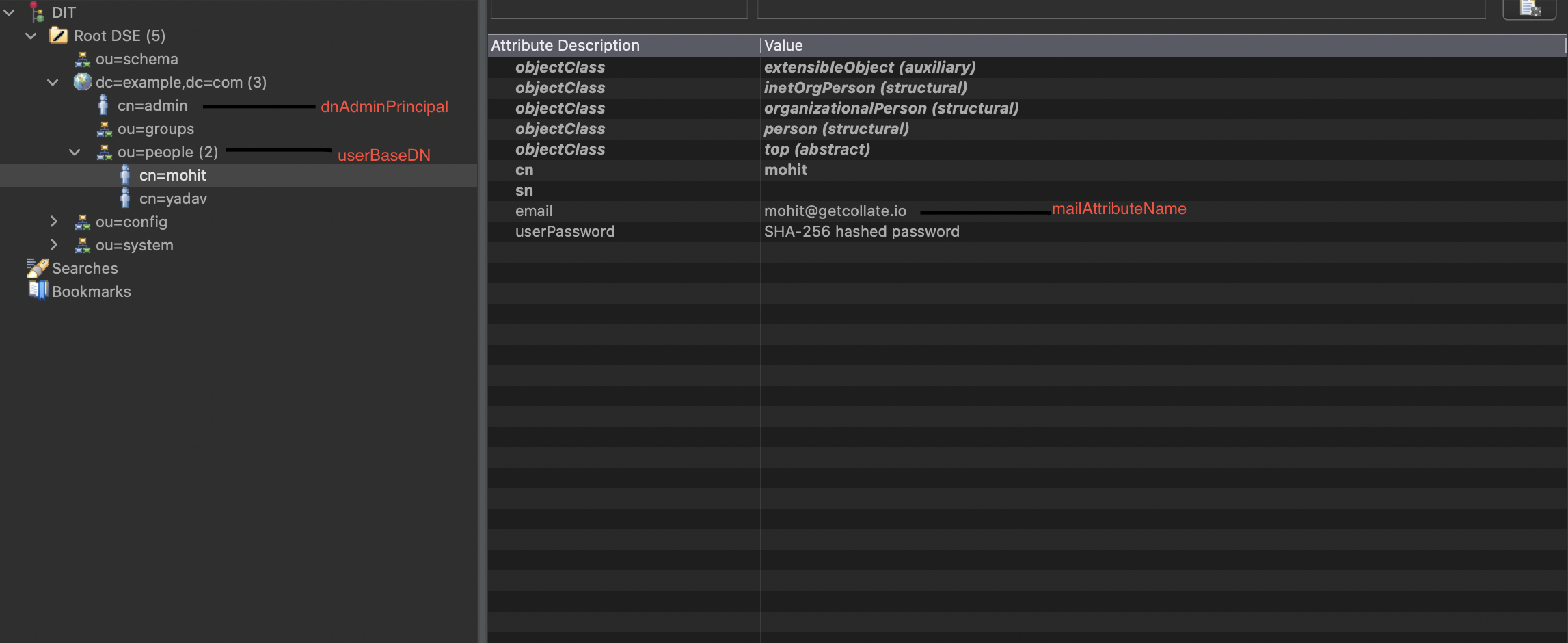
host: hostName for the Ldap Server (Ex - localhost).port: port of the Ldap Server to connect to (Ex - 10636).dnAdminPrincipal: This is the DN Admin Principal(Complete path Example :- cn=admin,dc=example,dc=com ) with a lookup access in the Directory.dnAdminPassword: Above Admin Principal Password.userBaseDN: User Base DN(Complete path Example :- ou=people,dc=example,dc=com).
Please see the below image for a sample LDAP Configuration in ApacheDS.
Advanced LDAP Specific Configuration (Optional):
maxPoolSize: Connection Pool Size to use to connect to LDAP Server.sslEnabled: Set to true if the SSL is enable to connect to LDAP Server.truststoreConfigType: Truststore type. It is required. Can select from {CustomTrustStore, HostName, JVMDefault, TrustAll}trustStoreConfig: Config for the selected truststore type. Please check below note for setting this up.
Based on the different truststoreConfigType, we have following different trustStoreConfig.
- TrustAll: Provides an SSL trust manager which will blindly trust any certificate that is presented to it, although it may optionally reject certificates that are expired or not yet valid. It can be convenient for testing purposes, but it is recommended that production environments use trust managers that perform stronger validation.
examineValidityDates: Indicates whether to reject certificates if the current time is outside the validity window for the certificate.
- JVMDefault: Provides an implementation of a trust manager that relies on the JVM's default set of trusted issuers.
verifyHostname: Controls using TrustAllSSLSocketVerifier vs HostNameSSLSocketVerifier. In case the certificate contains cn=hostname of the Ldap Server set it to true.
- HostName: Provides an SSL trust manager that will only accept certificates whose hostname matches an expected value.
allowWildCards: Indicates whether to allow wildcard certificates which contain an asterisk as the first component of a CN subject attribute or dNSName subjectAltName extension.acceptableHostNames: The set of hostnames and/or IP addresses that will be considered acceptable. Only certificates with a CN or subjectAltName value that exactly matches one of these names (ignoring differences in capitalization) will be considered acceptable. It must not be null or empty.
- CustomTrustStore: Use the custom Truststore by providing the below details in the config.
trustStoreFilePath: The path to the trust store file to use. It must not be null.trustStoreFilePassword: The PIN to use to access the contents of the trust store. It may be null if no PIN is required.trustStoreFileFormat: The format to use for the trust store. (Example :- JKS, PKCS12).verifyHostname: Controls using TrustAllSSLSocketVerifier vs HostNameSSLSocketVerifier. In case the certificate contains cn=hostname of the Ldap Server set it to true.examineValidityDates: Indicates whether to reject certificates if the current time is outside the validity window for the certificate.
Authorizer Configuration
This configuration controls the authorizer for OpenMetadata:
For the Ldap we need to set:
adminPrincipals: This is the list of admin Principal for the OpenMetadata , if mail in ldap is example@open-metadata.org, then if we want this user to be admin in the OM, we should add 'example', in this list.principalDomain: Company Domain.
Configure Ingestion
Once your server security is set, it's time to review the ingestion configuration. Our bots support JWT tokens to authenticate to the server when sending requests.
Find more information on Enabling JWT Tokens and JWT Troubleshooting to ensure seamless authentication.