Keycloak SSO
Follow the sections in this guide to set up Keycloak SSO.
Security requirements for your production environment:
- DELETE the admin default account shipped by OM in case you had Basic Authentication enabled before configuring the authentication with Keycloak SSO.
- UPDATE the Private / Public keys used for the JWT Tokens. The keys we provide by default are aimed only for quickstart and testing purposes. They should NEVER be used in a production installation.
Create Server Credentials
Step 1: Access the Keycloak Admin Console
- You need an administrator account. If you don't have, see Creating the first administrator.
- Go to the URL for the Admin Console. For example, for localhost, use this URL: http://localhost:8080/admin/
- Enter the username and password you created.
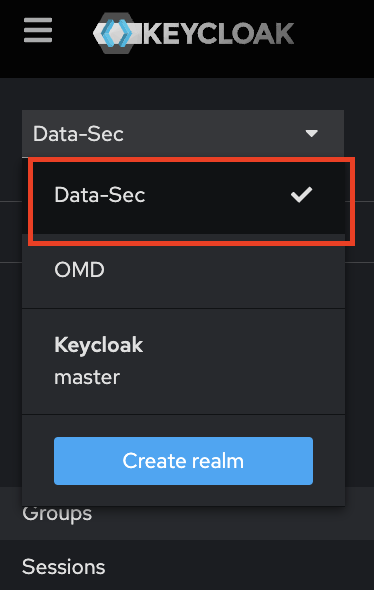
Step 2: Change Realm selected
- The Keycloak use Realms as the primary form of organization, we can't use the realm "master" for new clients (apps), only for administration, so change for your specific realm or create a new.
- In this example we are used an existing one called "Data-sec".
Create Server Credentials
Choose Your Authentication Flow
After creating the account, choose the authentication flow you want to use:
- Implicit Flow (Public)
- Auth Code Flow (Confidential)
SPA (Single Page Application):
This type is designed for implicit flows. In this case, providing both the client ID and client secret will result in a failure because the implicit flow only requires the client ID for authentication.Web:
This type is intended for confidential clients. If you select this option, you must provide both the client ID and client secret. Simply passing the client ID will cause the authorization process to fail, as the Authorization Code flow requires both credentials for successful authentication. The OIDC Authorization Code Flow is used in this case, where the client secret is required to securely exchange the authorization code for tokens.
Recommendation:
- Use the Web type for confidential clients that require both a client ID and secret.
- Use the SPA type for applications using implicit flows where only a client ID is needed.
Configure Ingestion
Once your server security is set, it's time to review the ingestion configuration. Our bots support JWT tokens to authenticate to the server when sending requests.
Find more information on Enabling JWT Tokens and JWT Troubleshooting to ensure seamless authentication.